寄稿しました。
会社内のESXi上にVulsサーバを設置し、外部のサーバ群の脆弱性を管理しています…(๑❛ᴗ❛๑ )
もくじ
Vulsサーバのインストール+設定
開発系+基本インストール
# yum groupinstall "Development Tools" # yum groupinstall "Base" # yum install gcc gcc-c++ pcre-devel zlib-devel make wget openssl-devel libxml2 libxml2-devel libxslt-devel libxslt libxslt-devel gd-devel perl-ExtUtils-Embed GeoIP-devel gperftools-devel flex libmcrypt libtool-ltdl libtidy libXpm libtiff gd-last autoconf automake gmp gmp-devel libgmp.so.3 libssl.so.6 # yum install curl-devel expat-devel gettext-devel openssl-devel zlib-devel perl-ExtUtils-MakeMaker # yum install sqlite git gcc make yum-plugin-changelog
# yum update
# reboot now
Vuls用ユーザの作成
# useradd vulsuser # passwd vulsuser
# visudo ## Allows people in group wheel to run all commands %wheel ALL=(ALL) ALL ※下記を追加 Defaults:vuls !requiretty vulsuser ALL=(root) NOPASSWD: ALL Defaults:vuls env_keep="http_proxy https_proxy HTTP_PROXY HTTPS_PROXY"
ここからVuls用ユーザで作業します。
# su - vulsuser
公開鍵認証用の鍵ペアを作る
$ ssh-keygen -t rsa -b 4096
$ cat id_rsa -----BEGIN RSA PRIVATE KEY----- MIIJKQjjoidsofijdslkfjlakfopoerdpotdj53498vl;sgfdgazAdflk$#sdfaf MnQo889W9WMCGvwlcDX2Ml1VgaQuDdtZLd8+ER+AWdi/pdtrXBaqjkqe5Zkr802n A705NYPnn76kLfhaBAWw/vQXD819ufk7PBpLCDEbj23iz/b7/Lm47oxhtRW28gRM MIIJKQjjoidsofijdslkfjlakfopoerdpot53498vl;sgfdgazAdfgslk$#sdfaf MnQo889W9WMCGvwlcDX2Ml1VgaQuDdtZLd8+ER+AWdi/pdtrXBaqjkqe5Zkr802n A705NYPnn76kLfhaBAWw/vQXD819ufk7PBpLCDEbj23iz/b7/Lm47oxhtRW28gRM (略) MIIJKQjjoidsofijdslkfjlakfopoerdpot53498vl;sgfdgazAdfgslk$#sdfaf MnQo889W9WMCGvwlcDX2Ml1VgaQuDdtZLd8+ER+AWdi/pdtrXBaqjkqe5Zkr802n A705NYPnn76kLfhaBAWw/vQXD819ufk7PBpLCDEbj23iz/b7/Lm47oxhtRW28gRM l0URzEnbBmFZ0L3hOGDn678G7aO4vffGEvEP9LvF0CbXXJ93iP6EkxK0ZV80 -----END RSA PRIVATE KEY-----
$ cat id_rsa.pub ssh-rsa oiwto4tp42AFDSfoEBbD+9BcPzX25+Ts8GksIMRuPbeLP9vv8ubjujGG1FbbyBExpqLWVOa2/eXpkYIVnGUzEExQ/UiJzVTZw1uifS/LGydcOXFEFvLsYUmFUQjoXpLIxyf76FXLWg1JXLlKC8zzC3f3A+xN3RVtxTbWUv6eu2UPhBaItCwrNQqDaQSRfCSDioY472wlW23fXSQLMpVpqeyvQzoDGHJ0UByPsVMk8PXqyegG5wg/qC/ujlbSbirAnVjX5d/mxQRDs8ynZF85YtX8LwyCTZBu3uzkUoMIHovmLKDFs3duw8IPEc9QtRK6x0y5z2V9L4c1H/8YpJww57HUzzEbbuvjihMt1kpnrpNrB4lPVGtoV0nGVLhQ86djAZQPurfvT0dyEO0sFWDSRTWEj/zh==
パーミッション設定
$ sudo chmod 700 /home/vulsuser/.ssh $ sudo chmod 400 /home/vulsuser/.ssh/id_rsa $ mv /home/vulsuser/.ssh/id_rsa.pub /home/vulsuser/.ssh/authorized_keys $ sudo chmod 600 /home/vulsuser/.ssh/authorized_keys
SSH設定
$ sudo vi /etc/ssh/sshd_config #Port 22 Port xxx22 #PermitRootLogin yes PermitRootLogin no #PasswordAuthentication yes PasswordAuthentication no
$ sudo sshd -t $ sudo systemctl reload sshd
Go言語インストール
$ cd
https://golang.org/dl/ $ wget https://storage.googleapis.com/golang/go1.9.linux-amd64.tar.gz
$ sudo tar -C /usr/local -xzf go1.9.linux-amd64.tar.gz $ mkdir $HOME/go $ ls go go1.9.linux-amd64.tar.gz $ rm go1.9.linux-amd64.tar.gz
環境変数設定
$ sudo vi /etc/profile.d/goenv.sh export GOROOT=/usr/local/go export GOPATH=$HOME/go export PATH=$PATH:$GOROOT/bin:$GOPATH/bin
反映させる
$ sudo chmod 755 /etc/profile.d/goenv.sh $ source /etc/profile.d/goenv.sh $ go version go version go1.9 linux/amd64
辞書ファイルライブラリのインストール
$ sudo mkdir /var/log/vuls $ sudo chown vulsuser /var/log/vuls $ sudo chmod 700 /var/log/vuls $ mkdir -p $GOPATH/src/github.com/kotakanbe
$ cd $GOPATH/src/github.com/kotakanbe $ pwd /home/vulsuser/go/src/github.com/kotakanbe $ git clone https://github.com/kotakanbe/go-cve-dictionary.git Cloning into 'go-cve-dictionary'... remote: Counting objects: 500, done. remote: Total 500 (delta 0), reused 0 (delta 0), pack-reused 500 Receiving objects: 100% (500/500), 142.72 KiB | 64.00 KiB/s, done. Resolving deltas: 100% (259/259), done. $ cd go-cve-dictionary $ make install go get -u github.com/golang/dep/... dep ensure go install -ldflags "-X 'main.version=v0.1.1' -X 'main.revision=f5406ff'"
エラーが出る場合
古いバージョンのgoが残っているパターンの場合
go get -u github.com/golang/dep/…
go install runtime/internal/atomic: open /usr/local/go/pkg/linux_amd64/runtime/internal/atomic.a: permission denied
make: *** [dep] Error 1エラー
$ cd /usr/local
$ ls -laht
total 287M
drwxr-xr-x 13 root root 4.0K Sep 27 21:18 .
drwxr-xr-x 13 root root 4.0K Sep 26 14:49 ..
-rw-r–r– 1 root root 286M Aug 25 07:44 go1.9.linux-amd64.tar
drwxr-xr-x 11 root root 4.0K Aug 25 06:51 go
$ sudo rm -rf /usr/local/go
脆弱性データベース取得
$ cd $HOME $ pwd /home/vulsuser NVD 約10分 $ for i in `seq 2002 $(date +"%Y")`; do go-cve-dictionary fetchnvd -years $i; done JVN 約5分 $ for i in `seq 1998 $(date +"%Y")`; do go-cve-dictionary fetchjvn -years $i; done
Redhat系脆弱性情報取得 CentOS5, 6, 7
$ cd $GOPATH/src/github.com/kotakanbe $ git clone https://github.com/kotakanbe/goval-dictionary.git $ cd goval-dictionary $ make install fatal: No names found, cannot describe anything. go get -u github.com/golang/dep/... dep ensure go install -ldflags "-X 'main.version=' -X 'main.revision=fd8ff5a'" $ goval-dictionary fetch-redhat -dbpath=$HOME/oval.sqlite3 5 6 7
Vulsのインストール
$ mkdir -p $GOPATH/src/github.com/future-architect $ cd $GOPATH/src/github.com/future-architect $ pwd /home/vulsuser/go/src/github.com/future-architect $ git clone https://github.com/future-architect/vuls.git Cloning into 'vuls'... remote: Counting objects: 3756, done. remote: Compressing objects: 100% (32/32), done. remote: Total 3756 (delta 17), reused 22 (delta 11), pack-reused 3711 Receiving objects: 100% (3756/3756), 3.94 MiB | 1.13 MiB/s, done. Resolving deltas: 100% (2564/2564), done. $ cd vuls vuls]$ make install go get -u github.com/golang/dep/... dep ensure go install -ldflags "-X 'main.version=v0.4.0' -X 'main.revision=e5eb8e4'"
コンフィグ設定
$ vi /home/vulsuser/config.toml [email] smtpAddr = "localhost" smtpPort = "25" from = "VulsServer@example.net" to = ["hoge@gmail.com"] subjectPrefix = "[vuls]" [servers] # localhost [servers.localhost] host = "localhost" port = "local" # HOGEサーバ [servers.HOGE] host = "153.xxx.yyy.17" port = "xxx22" user = "vulsuser" keyPath = "/home/vulsuser/.ssh/id_rsa" # MOGEサーバ [servers.MOGE] host = "153.xxx.yyy.46" port = "xxx22" user = "vulsuser" keyPath = "/home/vulsuser/.ssh/id_rsa"
“クライアント側”サーバ作業 ※検査される対象
# useradd vulsuser # su - vulsuser $ mkdir .ssh Vulsサーバで作った公開鍵を貼り付ける。 $ vi ~/.ssh/authorized_keys ssh-rsa oiwto4tp42AFDSfoEBbD+9BcPzX25+Ts8GksIMRuPbeLP9vv8ubjujGG1FbbyBExpqLWVOa2/eXpkYIVnGUzEExQ/UiJzVTZw1uifS/LGydcOXFEFvLsYUmFUQjoXpLIxyf76FXLWg1JXLlKC8zzC3f3A+xN3RVtxTbWUv6eu2UPhBaItCwrNQqDaQSRfCSDioY472wlW23fXSQLMpVpqeyvQzoDGHJ0UByPsVMk8PXqyegG5wg/qC/ujlbSbirAnVjX5d/mxQRDs8ynZF85YtX8LwyCTZBu3uzkUoMIHovmLKDFs3duw8IPEc9QtRK6x0y5z2V9L4c1H/8YpJww57HUzzEbbuvjihMt1kpnrpNrB4lPVGtoV0nGVLhQ86djAZQPurfvT0dyEO0sFWDSRTWEj/zh== $ chmod 700 .ssh $ chmod 600 ~/.ssh/authorized_keys
Vulsサーバ側作業
クライアント側サーバに手動で1度ログインを行うことで、クライアントのknown_hostsに登録する。※これを行わないとエラーになる。
$ ssh vulsuser@153.xxx.yyy.46 -p 35522 -i /home/vulsuser/.ssh/id_rsa (略) Are you sure you want to continue connecting (yes/no)? yes $ ssh vulsuser@153.xxx.yyy.17 -p 35522 -i /home/vulsuser/.ssh/id_rsa (略) Are you sure you want to continue connecting (yes/no)? yes
コンフィグテスト
$ cd $HOME $ vuls configtest [Sep 28 18:30:38] INFO [localhost] Validating config... [Sep 28 18:30:38] INFO [localhost] Detecting Server/Container OS... [Sep 28 18:30:38] INFO [localhost] Detecting OS of servers... [Sep 28 18:30:38] INFO [localhost] (1/3) Detected: localhost: centos 7.4.1708 [Sep 28 18:30:39] INFO [localhost] (2/3) Detected: MOGE: centos 6.8 [Sep 28 18:30:41] INFO [localhost] (3/3) Detected: HOGE: centos 7.4.1708 [Sep 28 18:30:41] INFO [localhost] Detecting OS of containers... [Sep 28 18:30:41] INFO [localhost] Checking dependencies... [Sep 28 18:30:41] INFO [localhost] Dependencies ... Pass [Sep 28 18:30:42] INFO [MOGE] Dependencies ... Pass [Sep 28 18:30:42] INFO [HOGE] Dependencies ... Pass [Sep 28 18:30:42] INFO [localhost] Checking sudo settings... [Sep 28 18:30:42] INFO [HOGE] sudo ... No need [Sep 28 18:30:42] INFO [localhost] sudo ... No need [Sep 28 18:30:42] INFO [MOGE] sudo ... No need [Sep 28 18:30:42] INFO [localhost] Scannable servers are below... HOGE localhost MOGE
スキャン開始!
$ vuls scan [Sep 28 18:31:05] INFO [localhost] Start scanning [Sep 28 18:31:05] INFO [localhost] config: /home/vulsuser/config.toml [Sep 28 18:31:05] INFO [localhost] Validating config... [Sep 28 18:31:05] INFO [localhost] Detecting Server/Container OS... [Sep 28 18:31:05] INFO [localhost] Detecting OS of servers... [Sep 28 18:31:05] INFO [localhost] (1/3) Detected: localhost: centos 7.4.1708 [Sep 28 18:31:06] INFO [localhost] (2/3) Detected: MOGE: centos 6.8 [Sep 28 18:31:08] INFO [localhost] (3/3) Detected: HOGE: centos 7.4.1708 [Sep 28 18:31:08] INFO [localhost] Detecting OS of containers... [Sep 28 18:31:08] INFO [localhost] Detecting Platforms... [Sep 28 18:31:20] INFO [localhost] (1/3) HOGE is running on other [Sep 28 18:31:20] INFO [localhost] (2/3) localhost is running on other [Sep 28 18:31:20] INFO [localhost] (3/3) HOGE is running on other [Sep 28 18:31:20] INFO [localhost] Scanning vulnerabilities... [Sep 28 18:31:20] INFO [localhost] Scanning vulnerable OS packages... One Line Summary ================ localhost centos7.4.1708 0 updatable packages [Reboot Required] HOGE centos7.4.1708 0 updatable packages [Reboot Required] MOGE centos6.8 212 updatable packages
ショートテキスト
$ vuls report -format-short-text -cvedb-path=$PWD/cve.sqlite3 --lang=ja -ovaldb-path $HOME/oval.sqlite3 -cvss-over=7 [Sep 28 03:22:00] INFO [localhost] Validating config... [Sep 28 03:22:00] INFO [localhost] cve-dictionary: /home/vulsuser/cve.sqlite3 [Sep 28 03:22:00] INFO [localhost] Loaded: /home/vulsuser/results/2017-09-28T03:21:31+09:00 [Sep 28 03:22:00] INFO [localhost] Fill CVE detailed information with OVAL [Sep 28 03:22:00] WARN [localhost] OVAL entries of redhat 6 are not found. It's recommended to use OVAL to improve scanning accuracy. For details, see https://github.com/kotakanbe/goval-dictionary#usage , Then report with --ovaldb-path or --ovaldb-url flag [Sep 28 03:22:00] INFO [localhost] Fill CVE detailed information with CVE-DB [Sep 28 03:22:00] INFO [localhost] Fill CVE detailed information with OVAL [Sep 28 03:22:00] WARN [localhost] OVAL entries of redhat 7 are not found. It's recommended to use OVAL to improve scanning accuracy. For details, see https://github.com/kotakanbe/goval-dictionary#usage , Then report with --ovaldb-path or --ovaldb-url flag [Sep 28 03:22:00] INFO [localhost] Fill CVE detailed information with CVE-DB [Reboot Required] MOGE (centos6.8) =================================== Total: 0 (High:0 Medium:0 Low:0 ?:0) 212 updatable packages No CVE-IDs are found in updatable packages. 212 updatable packages [Reboot Required] localhost (centos7.4.1708) ============================================ Total: 0 (High:0 Medium:0 Low:0 ?:0) 0 updatable packages No CVE-IDs are found in updatable packages. 0 updatable packages
フルテキストバージョン
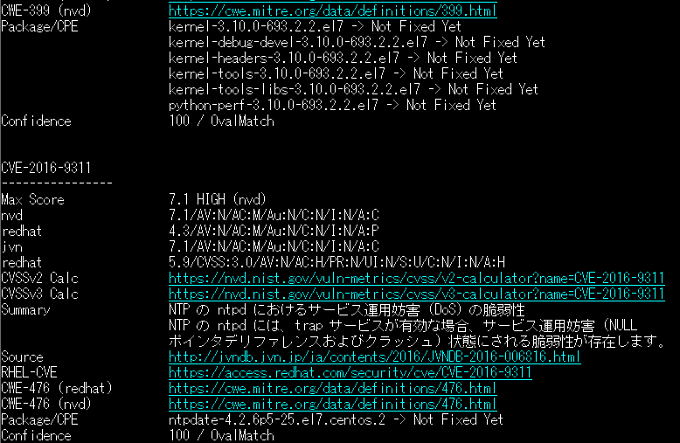
こんな風に出ます。
$ vuls report -format-full-text -cvedb-path=$PWD/cve.sqlite3 -ovaldb-path $HOME/oval.sqlite3 -cvss-over=7 --lang=ja
TUIモード
$ vuls tui
メール送信
$ vuls report -format-full-text -cvedb-path=$PWD/cve.sqlite3 -ovaldb-path $HOME/oval.sqlite3 -cvss-over=7 --lang=ja -format-one-email -to-email
脆弱性情報DBの更新
$ go-cve-dictionary fetchnvd -last2y -dbpath=$HOME/cve.sqlite3 > /dev/null 2>&1 $ go-cve-dictionary fetchjvn -last2y -dbpath=$HOME/cve.sqlite3 > /dev/null 2>&1 $ goval-dictionary fetch-redhat -dbpath=$HOME/oval.sqlite3 5 6 7 > /dev/null 2>&1
定期実行設定
メール, 送信テスト
# yum install mailx # echo "root送信テスト2206" | mail -s "mail2206" root
$ sudo vi /root/vulscheck.sh #!/bin/bash ## =========================== VULS_USER=vulsuser ## =========================== cd /home/$VULS_USER # CVE, OVALアップデート go-cve-dictionary fetchnvd -last2y -dbpath=$HOME/cve.sqlite3 > /dev/null 2>&1 go-cve-dictionary fetchjvn -last2y -dbpath=$HOME/cve.sqlite3 > /dev/null 2>&1 goval-dictionary fetch-redhat -dbpath=$HOME/oval.sqlite3 5 6 7 > /dev/null 2>&1 # スキャンとメール送信 /home/$VULS_USER/go/bin/vuls report -format-full-text -cvedb-path=$PWD/cve.sqlite3 -ovaldb-path $HOME/oval.sqlite3 -cvss-over=7 --lang=ja -format-one-email -to-email > /dev/null 2>&1
$ sudo chmod +x /root/vulscheck.sh
テスト実行
$ sudo /root/vulscheck.sh
Crontabに登録します。
# sudo vi /etc/crontab SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin MAILTO='' # For details see man 4 crontabs # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed ## 日曜 朝6時30分にVulsによるチェックを行う 30 6 * * 7 vulsuser /root/vulscheck.sh
反映させます。
$ sudo systemctl enable crond $ sudo systemctl restart crond
VulsRepoのインストール
VulsRepoのインストール
$ cd $ git clone https://github.com/usiusi360/vulsrepo.git $ cd $HOME/vulsrepo/server $ cp vulsrepo-config.toml.sample vulsrepo-config.toml
設定を編集します。
$ vi vulsrepo-config.toml [Server] rootPath = "/home/vuls-user/vulsrepo" resultsPath = "/opt/vuls/results" serverPort = "5111" #[Auth] #authFilePath = "/home/vuls-user/.htdigest" #realm = "vulsrepo_local" ↓変更 [Server] rootPath = "/home/vulsuser/vulsrepo" resultsPath = "/home/vulsuser/results" serverPort = "5111" #[Auth] #authFilePath = "/home/vulsuser/.htdigest" #realm = "vulsrepo_local"
$ pwd /home/vulsuser/vulsrepo/server
サーバ起動
$ nohup ./vulsrepo-server &
※$ nohup スクリプト &
ログアウト後もバックグラウンドでスクリプトが継続して動きます。
アクセスする